Exhaustion Mac OS
Are you one of the millions of Mac users under the impression that your digital security is guaranteed simply due to the fact that you’re using a Mac? Then I’ve got some news for you that you may not want to hear: the popular and long-standing myth that Mac users are immune to security vulnerabilities is just that -- a myth. This myth largely derives from the fact that the global Windows market share dwarfs that of macOS. Hackers and cybercriminals would much rather target an operating system that serves nearly 90 percent of users worldwide than one that accounts for less than 10 percent.
- Exhaustion Mac Os 11
- Exhaustion Mac Os Catalina
- Exhaustion Mac Os X
- Exhaustion Makes Cowards Of Us All
- Exhaustion Mac Os Download
The truth is that Macs are still very much susceptible to vulnerabilities that can be exploited by cybercriminals, or even by developers of apps you may use on a daily basis. So if you’re a Mac user who has been lulled into a false sense of security, it’s time for you to wake up and realize that your security is by no means guaranteed on a Mac. That’s the hard reality of it, and the sooner you come to grips with it, the sooner you can start taking steps to protect your digital security and personal privacy on your Mac.
Mac OS X Dashboard Widget: Download. Hurricane Electric 760 Mission Court Fremont, CA 94539 Voice +1 (510) 580-4100 Fax +1 (510) 580-4151 Comments? Mac OS X 10.7 (Lion) Yes Yes Yes: Yes: Versions 10.7 through 10.10 often prefer IPv4 even when working IPv6 connectivity is available. Versions 10.11 and up will prioritize IPv6 Traffic in spec with Happy Eyeballs. MeeGo: 1.2 No: Yes: No Yes: NetBSD: 7.0 Yes Yes Yes Yes OpenBSD: 6.6 Yes Yes Addon: Yes. Mac OS X 10.6 (Snow Leopard) introduces support for ISAKMP Delete messages, therefore if you have this version or later it is recommended to enable the ISAKMP Delete messages. See the ro uter ISAKMP configuration section for more comments. Support for NAT-T For full inter-operable support of NAT-T we recommend using Mac OS X 10.5 or later.
Even after knowing that your Mac isn’t immune to vulnerabilities, you may still think that only hackers and cybercriminals would be a threat to the security of your Mac. Unfortunately, that isn’t the case. Bugs lurking undetected within some of the applications you may use on a daily basis could easily leave you exposed to a potential malicious attacker. What’s even more frightening, app developers themselves may be reluctant to squash those bugs even after they have been detected and reported to the company developing the application.
Case in point is the recent revelation that the popular video conferencing app, Zoom, contained a vulnerability that allowed for a third-party actor to remotely enable Mac users’ microphones and cameras without their permission simply by having the victim click on a Zoom meeting link. In March, a cybersecurity researcher responsibly disclosed to the company a number of serious vulnerabilities contained within the Zoom application. The most egregious of which was the aforementioned camera vulnerability that was made possible by a local web server that was automatically installed with the Zoom application on Mac computers. The local web server was installed in the background as a way for Zoom to create a seamless video conferencing experience for its Mac users. Essentially, it made it possible for the software to bypass a security feature in the Safari web browser that required user confirmation prior to launching the app on a Mac, thus saving the user a mouse click or two by automatically launching the app without having to click the confirmation dialogue.
It turns out that this vulnerability could easily be exploited by a malicious actor and used as a way to remotely hijack unsuspecting Mac users’ cameras and microphones, leaving them fully exposed to a flagrant invasion of privacy. Shockingly, according to the security researcher’s blog post, Zoom persistently attempted to downplay the seriousness of the vulnerability during ongoing conversations with the researcher over a 90-day period and was resistant to properly addressing the issue. Even after public disclosure of the vulnerability, Zoom initially continued to downplay the gravity of the issue and declined to take the researcher’s recommended action to remove the local webserver completely. Only after public backlash following the researcher’s disclosure did Zoom cave and agree to remove the webserver from an updated version of the app.
Ultimately, Zoom’s misguided notion that user experience trumps user security led the company to develop an application that allowed for potentially severe user privacy infringements. It is certainly alarming and indeed eye-opening for a company -- especially of Zoom’s stature -- to deliberately build into its software a way to bypass a browser security feature intended to protect Mac users’ privacy, even if it was in the interest of enhancing the user experience.
It can certainly be disheartening, but the Zoom case proves that your security may be at risk on your Mac even when using seemingly innocuous third-party applications. In these cases, it pays to take a close look at the app developer’s privacy policy and gain a full understanding of how the software works and what the company does specifically to protect your privacy when using its application. Pro tip: if the privacy policy is difficult to find or vague in its wording, then it’s probably best to look elsewhere.
If worrying about developers building security vulnerabilities into their applications isn’t enough, it’s important to understand that hackers and cybercriminals can absolutely target you even if you’re on your trusty Mac computer. The good news, though, is that there are concrete steps you can take to mitigate those cyber threats and minimize your chances of having your security compromised when using your Mac. You may think that antivirus software is only meant for Windows systems. However, since Macs can also be vulnerable to viruses and malware, cybersecurity experts have been increasingly recommending that Mac users install antivirus software as well.
Another necessary privacy tool to use on your Mac would be a virtual private network (VPN). By using a VPN on your Mac, you can secure your privacy by fully encrypting all of your internet traffic, essentially hiding everything you do online from hackers, cybercriminals, and even your internet service provider. A VPN is a simple and extremely effective way to stay secure and protect your privacy when using your Mac.
Exhaustion Mac Os 11
Although even Macs can be vulnerable to various cyber threats, there are certain steps you can take to ensure your privacy and security are properly maintained. It is fundamentally important to be aware of what security threats exist, and what you can do to counter them and keep yourself, and your Mac, safe and secure.
Photo credit:Angela Waye / Shutterstock
Attila Tomaschek is a digital privacy expert at ProPrivacy.com and a staunch advocate for a free and open internet. Attila is constantly investigating and analyzing matters of digital privacy and is always eager to share his knowledge with readers. Follow Attila on Twitter and LinkedIn.
These advanced steps are primarily for system administrators and others who are familiar with the command line. You don't need a bootable installer to upgrade macOS or reinstall macOS, but it can be useful when you want to install on multiple computers without downloading the installer each time.
What you need to create a bootable installer
- A USB flash drive or other secondary volume formatted as Mac OS Extended, with at least 14GB of available storage
- A downloaded installer for macOS Big Sur, Catalina, Mojave, High Sierra, or El Capitan
Download macOS
- Download: macOS Big Sur, macOS Catalina, macOS Mojave, or macOS High Sierra
These download to your Applications folder as an app named Install macOS [version name]. If the installer opens after downloading, quit it without continuing installation. To get the correct installer, download from a Mac that is using macOS Sierra 10.12.5 or later, or El Capitan 10.11.6. Enterprise administrators, please download from Apple, not a locally hosted software-update server. - Download: OS X El Capitan
This downloads as a disk image named InstallMacOSX.dmg. On a Mac that is compatible with El Capitan, open the disk image and run the installer within, named InstallMacOSX.pkg. It installs an app named Install OS X El Capitan into your Applications folder. You will create the bootable installer from this app, not from the disk image or .pkg installer.
Use the 'createinstallmedia' command in Terminal
- Connect the USB flash drive or other volume that you're using for the bootable installer.
- Open Terminal, which is in the Utilities folder of your Applications folder.
- Type or paste one of the following commands in Terminal. These assume that the installer is in your Applications folder, and MyVolume is the name of the USB flash drive or other volume you're using. If it has a different name, replace
MyVolumein these commands with the name of your volume.
Exhaustion Mac Os Catalina
Big Sur:*
Catalina:*
Exhaustion Mac Os X
Mojave:*
High Sierra:*
El Capitan:
* If your Mac is using macOS Sierra or earlier, include the --applicationpath argument and installer path, similar to the way this is done in the command for El Capitan.
After typing the command:
- Press Return to enter the command.
- When prompted, type your administrator password and press Return again. Terminal doesn't show any characters as you type your password.
- When prompted, type
Yto confirm that you want to erase the volume, then press Return. Terminal shows the progress as the volume is erased. - After the volume is erased, you may see an alert that Terminal would like to access files on a removable volume. Click OK to allow the copy to proceed.
- When Terminal says that it's done, the volume will have the same name as the installer you downloaded, such as Install macOS Big Sur. You can now quit Terminal and eject the volume.
Exhaustion Makes Cowards Of Us All
Use the bootable installer
Determine whether you're using a Mac with Apple silicon, then follow the appropriate steps:
Apple silicon
Exhaustion Mac Os Download
- Plug the bootable installer into a Mac that is connected to the internet and compatible with the version of macOS you're installing.
- Turn on your Mac and continue to hold the power button until you see the startup options window, which shows your bootable volumes.
- Select the volume containing the bootable installer, then click Continue.
- When the macOS installer opens, follow the onscreen instructions.
Intel processor
- Plug the bootable installer into a Mac that is connected to the internet and compatible with the version of macOS you're installing.
- Press and hold the Option (Alt) ⌥ key immediately after turning on or restarting your Mac.
- Release the Option key when you see a dark screen showing your bootable volumes.
- Select the volume containing the bootable installer. Then click the up arrow or press Return.
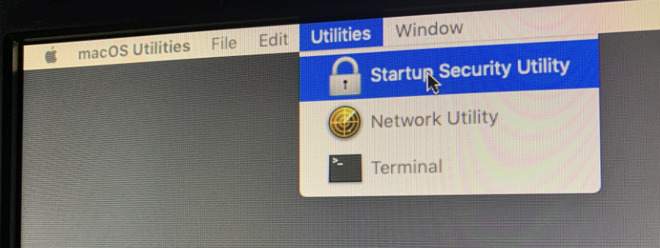
If you can't start up from the bootable installer, make sure that the External Boot setting in Startup Security Utility is set to allow booting from external media. - Choose your language, if prompted.
- Select Install macOS (or Install OS X) from the Utilities window, then click Continue and follow the onscreen instructions.
Learn more
A bootable installer doesn't download macOS from the internet, but it does require an internet connection to get firmware and other information specific to the Mac model.
For information about the createinstallmedia command and the arguments you can use with it, make sure that the macOS installer is in your Applications folder, then enter the appropriate path in Terminal: